Threat actors love phishing because it works. It is particularly effective in cloud infrastructure — once they’re inside, they gain access to anything else related to that cloud. According to Hornetsecurity’s Cybersecurity Report 2025, there were more than 471 million emails sent in 2024 that were flagged as “malicious.”
In terms of email attacks, phishing remained the top attack method at 33.3%. This makes it by far the most common attack vector, next to malicious URLs. But not all phishing is the same. Highly targeted phishing campaigns against specific individuals or types of individuals are known as spear phishing.
It’s important to be able to spot phishing in general. But for targets of spear phishing, it is even more essential to spot the telltale signs, as the damage done in these attacks tends to be greater.
What is phishing?
Phishing is basically an online version of fishing — except instead of marine life, the goal is to lure gullible users to reveal passwords and personal information by clicking on a malicious link or opening an attachment. Typical attacks are sent through email.
Sometimes, cybercriminals pose as representatives of cloud service providers and send messages related to a variety of online services and applications.
Phishing messages are often skillfully written. A common tactic is to impersonate reputable brands like Facebook and Microsoft, as well as banks, internet service providers, the IRS, and law enforcement agencies. These emails contain the appropriate logos to appear legitimate. Anyone following their directions and handing over their login details or clicking on a link is likely to infect their device, download malware, or be locked out of their network and asked to pay a ransom.
Once inside an application running in the cloud, threat actors can expand their attacks across more accounts and services. For example, breaching an organization’s Google or Microsoft cloud gives the attacker access to email accounts, contact lists, and document creation. By targeting a phishing campaign to obtain cloud credentials, the bad guys have a better chance of attracting a larger payload.
How can you identify a phishing email or message?
While phishing attempts can seem authentic, there are telltale signs which indicate that a message is part of a phishing attack. Here are a few to watch out for:
- Typographical or spelling errors.
- Unusual use of symbols or punctuation.
- Content is incoherent or poorly written.
- Message or email came from an unknown recipient.
- Uses generic greetings such as “Dear customer” or “Dear User.”
- Usually talks about something that’s too good to be true.
- Has suspicious links or file attachments.
What is spear phishing?
While phishing is generalized in that one phishing email may be sent to millions of people, spear phishing is highly targeted. The goal is to compromise the credentials of a specific person, such as the CEO or CFO of a company, as we reported on in 2023.
In spear phishing, the messaging is carefully crafted. Criminals study social media postings and profiles to obtain as much data as possible on a victim. They may even gain access to the person’s email and remain invisible for months while they evaluate the kind of traffic the person has coming in.
Spear phishing messages are designed to be far more believable than generic phishing attempts, as they are based on data taken from the person’s life and work. Reconnaissance makes the phishing email, text, or call very personalized.
In the cloud, a high-value target might be someone with administrative privileges for systems spanning thousands of individual accounts. By compromising that one identity, hackers have free rein to infect thousands more users.
SEE: Securing Linux Policy (TechRepublic Premium)
What is the main difference between phishing and spear phishing?
What distinguishes spear phishing from regular phishing is that the message generally has much more detail and adopts a tone of familiarity. The level of surprise and urgency is generally ramped up in spear phishing and often involves transferring money.
| Phishing | Spear Phishing | |
|---|---|---|
| Target | Mass or large group of people | Individual or group with authority (CEO, CFOs, IT admins) |
| Message’s level of detail | Low-to-medium | Very high |
| Tone of message | Generic or general | Portrays familiarity with target; personalized |
| Time frame | Done in one instance | Done over a long period of time |
| Depth of research required | Low | Very high |
| Method/medium | Text, call, online message, or email | Commonly done via business emails |
| End goal | Stealing a user’s credentials or obtaining small amounts of money from victim | Typically involves transferring large sums of money or confidential data |
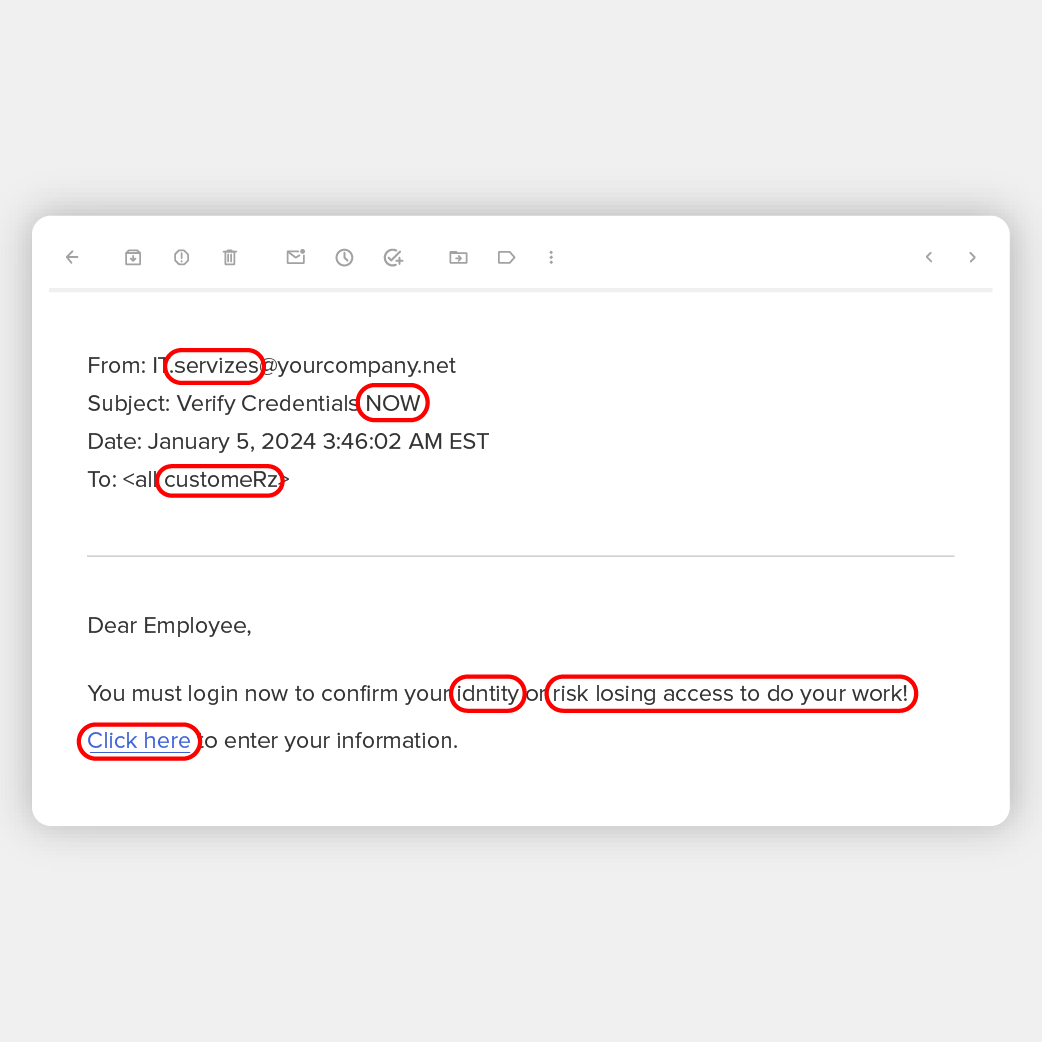
To be clear, many of the red flags for potential phishing emails also apply to spear phishing. They include typos in the text, bad grammar, emails from unknown recipients, suspicious links, a false sense of urgency, or requests via email to enter confidential information.
Phishing emails go to large quantities of people rather than to specific individuals. For example, an email might be sent to thousands of people or everyone in one company telling them that IT wants them to verify their credentials by clicking on a link and entering them on a form.
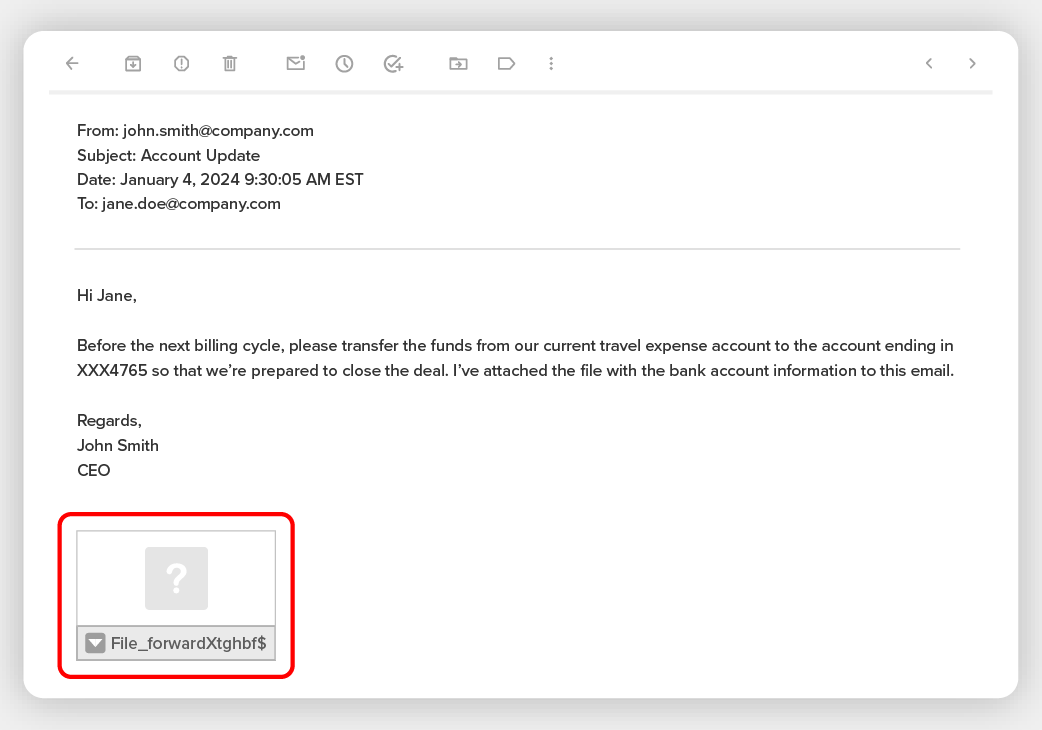
Spear phishing is more specific. For example, a CEO’s assistant might be targeted by a criminal who impersonates an email from the CEO. The hacker has been monitoring email messages and social media for months and knows that a big deal is about to go down at a point where the CEO is overseas, sealing the deal.
The criminal then sends an email that either looks like it is from the CEO or is even sent from the CEO’s account, telling the assistant there has been a change of plans and to transfer $x million to a new account immediately.
How to protect yourself from phishing and spear phishing
There are several steps that organizations can take to protect themselves from phishing and spear phishing attacks.
Install an anti-spam filter
A spam filter will catch up to 99% of spam and phishing emails. They are not infallible. But they do catch a lot of it. Spam filters are continually updated based on the latest scams and hacker tricks, so don’t go without one.
Use a VPN
A VPN is a virtual private network that provides those working remotely with greater privacy for messages than the internet. The user connects using an encrypted tunnel, which makes it difficult for anyone else to intercept the data. Using a VPN also makes it more difficult for phishers to succeed by adding additional layers of protection to email messaging and cloud usage.
Leverage multi-factor authentication (MFA) solutions
MFA should always be implemented. If someone does compromise a password, they can’t do any damage, as they need to be authenticated courtesy of an authenticator app, a code sent via text, a biometric, or some other authentication method.
Install antivirus software
Antivirus software was the original security safeguard that promised to prevent systems from getting infected by viruses. For a while, they did the job. But hackers figured out ways around them. Nevertheless, without it, a lot of malware would create havoc in the enterprise. Ensure antivirus software is part of your security arsenal, as it catches all manner of viruses and malware.
Implement cloud security posture management software
Cloud security posture management continuously monitors cloud risk via a combination of prevention, detection, response, and prediction steps that address areas where risk may appear next. This technology adds a predictive approach, which can make a big difference in cutting down on phishing and spear phishing scams.
This article was originally published in February 2024. It was updated by Luis Millares in January 2025.